Cybersecurity for Public Safety Officials
Vulnerability Management for Your PSAP
Trusted, reliable and comprehensive cybersecurity solutions to protect your data and secure your network – when every second counts.
Penetration Testing
Assess the strength of your network and identify vulnerabilities in the network, systems and devices against attacks that would allow bad actors to exploit these vulnerabilities and gain access to your network. This evaluation is a critical component in your cybersecurity plan to identify the weaknesses in your network that are putting your PSAP at risk of a data breach.
When partnering with Hamilton, our team of experts will help your PSAP:
Test Your Security Controls
Mitigate Vulnerabilities
Prevent Data Breaches

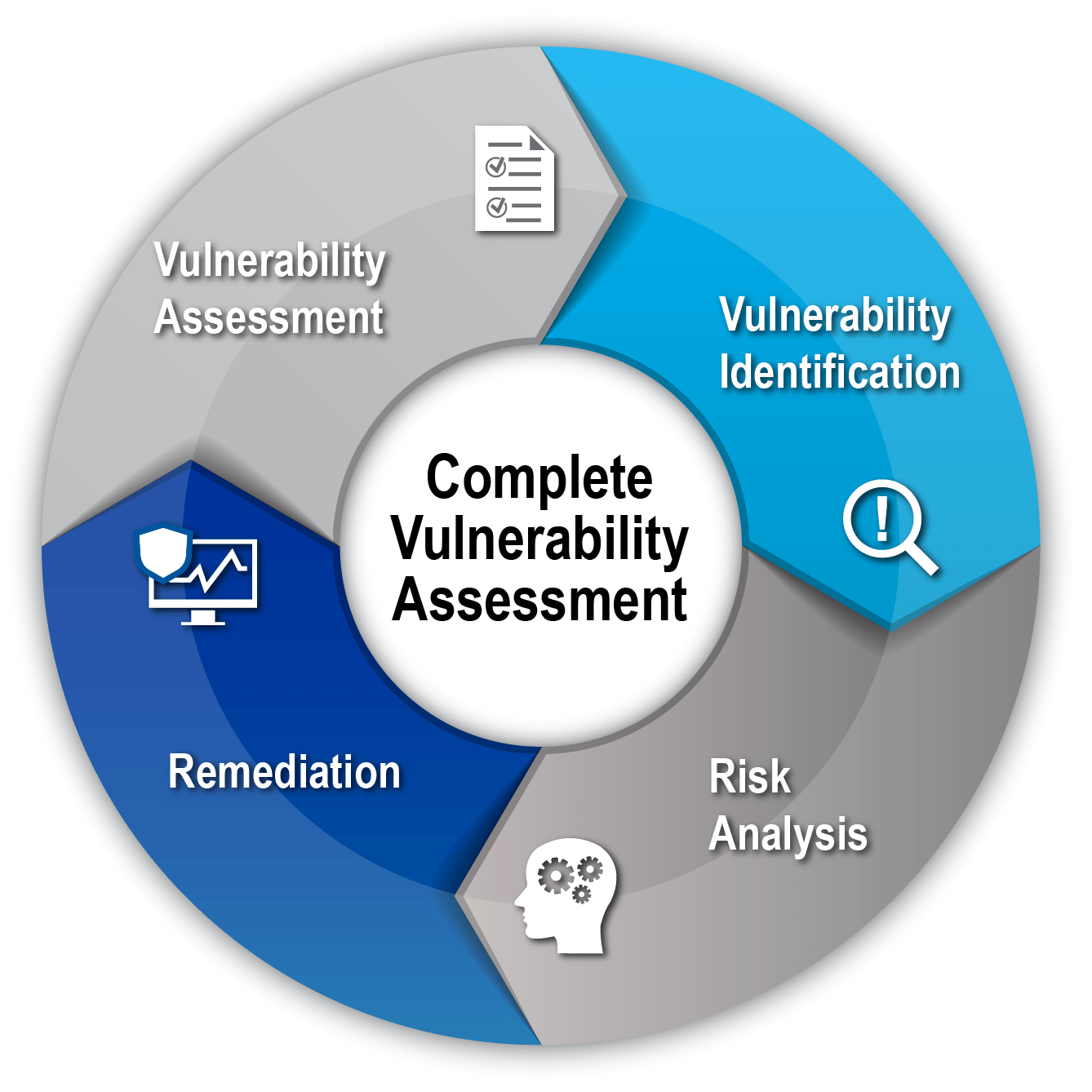
Complete Vulnerability Assessment
A systematic evaluation conducted within your network, systems, and infrastructure to identify potential security weaknesses, flaws, or vulnerabilities that could be exploited by bad actors or malicious software.
Stages of Vulnerability Assessment
Vulnerability Assessment
Vulnerability Identification
Risk Analysis
Remediation
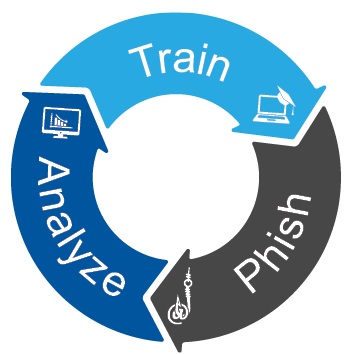
Phishing Simulations
Ensure your employees have the highest level of security awareness through continuous training and testing. Hamilton conducts phishing simulations with customized phishing tests and online courses.
Reduce the Human Risk
Reduce the Human Risk to your Network
Defend Against Changing Threats
Improve Employee security Awareness

Network Sentinel
Elevate your business with a comprehensive software stack designed to fortify your network, minimize risk, and proactively address any IT issues that may arise. As your trusted Managed IT service provider, we specialize in simplifying technology so you can focus on what matters most – growing your business.
Program Advantages
Advanced Security Protocols
Automated Monitoring and Response
Proactive Monitoring for Peace of Mind
Unlimited Support. Anytime, Anywhere.
Other IT Services
Offering a full suite of technology solutions that provide the tools and information you need for your PSAP.
Services
Managed IT
Business Phones
Data Center
Network Wiring & Cabling
Access Control & Security Solutions


